Fraudsters are licking their chops at the prospect of businesses and financial services extending remote working because of the coronavirus pandemic.
Such a scenario brings even more importance to cyberattackers' old standbys like stolen or weak passwords, social engineering and phishing — paired with human error or carelessness. That criminal toolbox will likely focus on the various security gaps between employee hardware and virtual data storage.
"As remote working surges in the face of the global pandemic, end-to-end security from the cloud to employee laptop becomes paramount," said Tami Erwin, CEO of Verizon Business. "In addition to protecting their systems from attack, we urge all businesses to continue employee education as phishing schemes become increasingly sophisticated and malicious."
In the past year, 37% of credential theft breaches used stolen or weak credentials, while 25% involved phishing and 22% resulted from human error, according to Verizon's 2020 Data Breach Investigations Report.
Verizon also reported a twofold increase, at 43%, in web application breaches, of which stolen credentials were used in more than 80% of the cases.
"This is a worrying trend, as business-critical workflows continue to move to the cloud," the report stated.
Use of ransomware had a slight increase to 27% of malware incidents, compared to 24% last year.
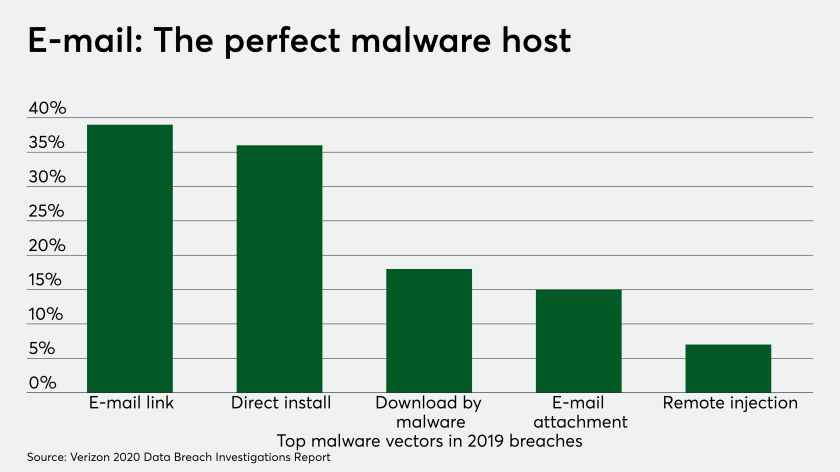
In compiling its annual report, Verizon's security team analyzed more than 32,000 security incidents, of which 3,950 were confirmed breaches — nearly double the number of breaches analyzed the previous year.
Organized crime rings were responsible for more than 50% of breaches, while nation-state or state-supported attacks accounted for about 10%. Others in the 10% range included system administrators, end users and unaffiliated attackers.
Employee Benefit News' March/April issue explores how workplaces are navigating pandemic challenges and making plans to return to the office.
The Internal Revenue Service released information on how employees now have until the end of the year to repay any payroll taxes they deferred from last year.
CPA firms will be in a great position to help their small business clients with the latest round of the Paycheck Protection Program, according to Barry Melancon.
Financial services organizations suffered web application attacks at 30%, making it one of the top causes for breaches. But there was a significant drop in misuse cases, in which an internal actor intentionally commits harm, to 8%, from 21.7% the previous year.
Cyberattacks can have common patterns, which enable organizations to determine the criminals' destination when discovering an attack in progress. Breach pathways like error, malware, physical or hacking help predict the eventual breach target. Organizations that set up ways to monitor the activity are in a far better position to gain a "defender's advantage," the report noted.
Attackers targeting credentials, personal data or payment information at small organizations deploy phishing techniques in more than 30% of attacks, followed by use of stolen credentials at 27% and password dumpers at 16%.
Nearly all attacks against retail operations were motivated by the financial reward of stealing payment or personal credentials to use for other attacks or spending sprees. Web applications, rather than the point of sale, have become the main cause of retail breaches, the report said.
Those findings fall in line with other security industry reports that indicate EMV chip card use at the point of sale has made the terminal far less attractive for criminals who instead concentrate on infiltrating networks and databases.
The numbers of reported attacks on large and small businesses have resulted in wide margins for the past seven years in the Verizon research, with the numbers for the 2020 report citing 407 incidents, and 221 with confirmed data disclosure for small businesses with fewer than 1,000 employees. By contrast, large businesses of more than 1,000 employees had 8,666 incidents, with 576 confirming data as stolen.

It makes security professionals wonder if small businesses still do not realize they have a problem, said Julie Conroy, research director at Aite Group.
"But the type of data that is targeted — shifting from payment card data in 2013 to personal credentials in 2020 — is not a surprise, given that EMV has made payment card data less valuable," Conroy said.
Mostly, businesses can expect external attacks and phishing to increase in the coming year, considering "the vast quantity of COVID related phishing we're seeing now," Conroy added.
The report confirms that warning, stating that the shift for businesses of all sizes to move to the cloud and its many web-based tools as a matter of advancing technology or in response to COVID-19, sets the stage for more social attacks.
"As small businesses have adjusted their business models, the criminals have adapted their actions in order to keep in step and select the quickest and easiest path to their victims," the report said.
Already, financial and insurance industries recorded 30% of breaches in the past year being caused by web application attacks, primarily driven through external actors using stolen credentials to get access to sensitive data stored in the cloud, the report noted.
In North America, hackers most often used stolen credentials, accounting for 79% of hacking breaches, with 33% using phishing.
In Europe, the Middle East and Africa, denial-of-service attacks accounted for more than 80% of malware incidents, while 40% of breaches targeted web applications using a combination of leveraging stolen credentials or known vulnerabilities.
"Security headlines often talk about spying, or grudge attacks, as the key driver for cybercrime, but our data shows that is not the case," said Alex Pinto, lead author of the Verizon report. "Financial gain continues to drive organized crime to exploit vulnerabilities or human error."
The good news is that if organizations learn to track common patterns in cyberattacks, it would be "a security game change" that puts control back into the hands of organizations around the globe, Pinto added.






